Do you need more storage?
The Run Down on Cloud Storage
The Rundown on External Hard DrivesExternal hard drives are little pocket-sized devices that can run as a USB plug-in hard drive. This means that you can keep your device with you and it's going to be faster and more reliable than a USB flash memory drive.
|
Congratulations you just bought a new computer. I am excited for you; it is one of the most fun moments you can have. Cracking that thing open or turning it on and getting in all the fun stuff!
|
Our Seven Steps for PC Success
Step 1: Security
|
Have problems with a new PC?
If you happen to have found this list a little bit after the fact and are running into some load errors, give us a call or send us an e-mail. We can help set your computer back up and ensure that no further problems occur. Give us a call if you need any help.
Why do you want a Laptop?
The main reason to choose a laptop over a desktop is because you need portability. Chances are it's a college effort or your business is relatively mobile. The other reason might be minimizing clutter in your office or home. But the fact is that Laptops, while being widespread, just aren't where they need to be yet.
|
The problems with Laptops and Mobile Devices
Computers are volatile and laptops are no exception
|
Have Laptop Issues?
Do you currently have a laptop that is giving you issues? We can help! Not only can we help you identify the better and necessary habits for proper laptop usage, but we can help you with maintaining and choosing your next computer, give us a call today!
What do I mean by your Apple ID becoming dusty? I mean that it is very easy to lose track of any of your accounts (email, banking, Amazon) if they seem to be working fine. Your browser or phone automatically logs you in, so there seems to be no need to keep up with your well-functioning accounts. Your Apple ID, like most of your other accounts, is actually two things: (a) An email and (b) a password.
The reason your Apple ID is different is that so much of your use of Apple products (even if you never buy any songs, apps, or movies) depends on your Apple ID. Your iPhone, iPad or Macintosh may be out of date because every time any of these devices tries to update itself, it prompts you for your Apple ID, and you don't know your Apple ID, so you forego updates (and possibly i-Cloud synchronization). Why? Because humans are not wired to keep track of more than a few arbitrary numbers or passwords. Until we have better methods (e.g., fingerprint, facial recognition, etc...), we are stuck with password logbooks.
I have seen this become increasingly important over the last year or so. So, what to do? Go to AppleID.com and check to see if your email/password combination works. If it doesn't, it is time to get out your little password logbook to see if you've forgotten your password. Now, be ready for Apple to send a 6-digit code to a secondary device in order to verify it's actually you.
Your Apple ID can get 'dusty' in the eyes of Apple. Best to keep it clear and clean by logging into AppleID.com and, once you know your Apple ID, log in to iCloud.com. The most honest representation of your Apple account, it's status, and what is synchronizing lie at AppleID.com and iCloud.com. Are your phone contacts synchronizing? Are your photos synchronizing? Do you have an old phone that you sold to Verizon that still shows up on your Apple account? You can check all these things at either AppleID.com or iCloud.com.
The reason your Apple ID is different is that so much of your use of Apple products (even if you never buy any songs, apps, or movies) depends on your Apple ID. Your iPhone, iPad or Macintosh may be out of date because every time any of these devices tries to update itself, it prompts you for your Apple ID, and you don't know your Apple ID, so you forego updates (and possibly i-Cloud synchronization). Why? Because humans are not wired to keep track of more than a few arbitrary numbers or passwords. Until we have better methods (e.g., fingerprint, facial recognition, etc...), we are stuck with password logbooks.
I have seen this become increasingly important over the last year or so. So, what to do? Go to AppleID.com and check to see if your email/password combination works. If it doesn't, it is time to get out your little password logbook to see if you've forgotten your password. Now, be ready for Apple to send a 6-digit code to a secondary device in order to verify it's actually you.
Your Apple ID can get 'dusty' in the eyes of Apple. Best to keep it clear and clean by logging into AppleID.com and, once you know your Apple ID, log in to iCloud.com. The most honest representation of your Apple account, it's status, and what is synchronizing lie at AppleID.com and iCloud.com. Are your phone contacts synchronizing? Are your photos synchronizing? Do you have an old phone that you sold to Verizon that still shows up on your Apple account? You can check all these things at either AppleID.com or iCloud.com.
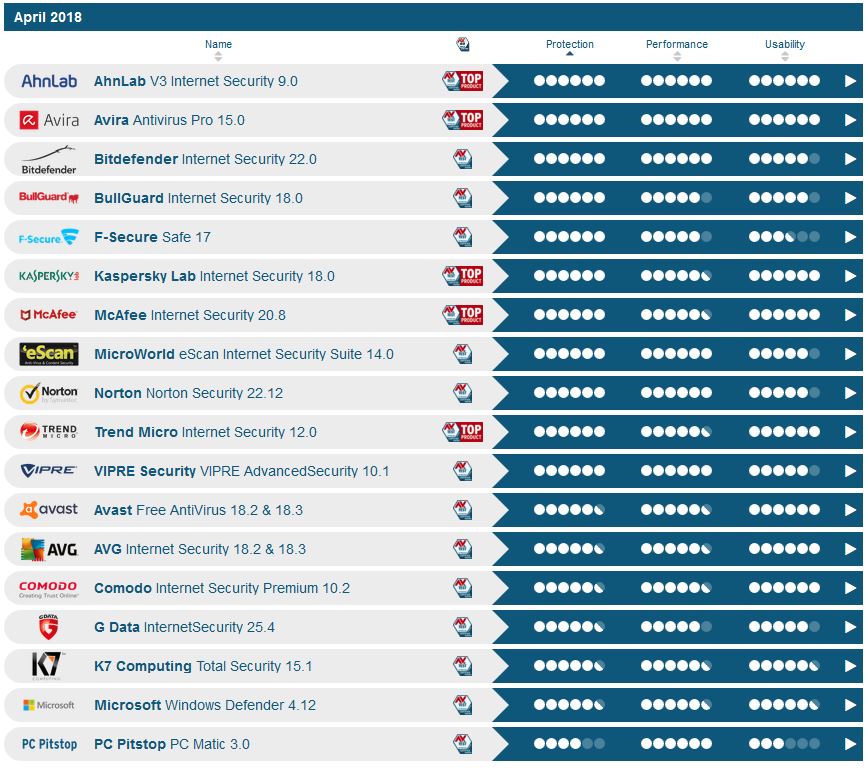
With all the choices in antivirus software, it is obvious that consumers wonder which one is best. The answer for the last five years or so has been: They're all good at protection, but some will interfere with benign activities on your PC more than others. I recommend Eset's NOD32, not because it's the best at protection, but instead because it is the least likely to 'gum up the works,' slow your PC down, or go off like an old radar detector or a nervous, bored dog who barks when a leaf blows.
In my testing, it is 10 times more important to keep your operating system, browsers, apps, and plugins up to date than it is to have the 'best' antivirus software.
How do I test for malware vulnerability? I create a dummy computer, put it on the Internet, and I visit Websites that are likely to (or are known to) infect computers with malware. Am I worried that the malware that I purposely expose my 'dummy' computer to will infect my other computers? No, because that's not how malware works anymore. Spreading to other PCs on a network is the behavior of older viruses, ones that were created more for vandalism and notoriety than to make money.
These are some of the things I learn from my malware testing:
-I find it more difficult to get my dummy computer infected than I thought it would be. The probable reason for this is that the dummy computer has not had time to collect the barnacles of spyware, adware, and browser hijacks that I end up finding on my customer's infected PCs.
-A PC with all legitimate updates applied, but no antivirus at all is much more secure than a PC with antivirus but no updates. Yes, even with top of the line antivirus, malware can get in.
The moral is: Malware defense is multi-faceted, and antivirus is typically not the most important facet. I would compare it to weight loss. Which is more important for losing weight, diet or exercise? Sadly, diet is typically more important for weight loss. In this analogy, I would compare diet to updates and exercise to antivirus.
In other words, regarding malware avoidance, an ounce of prevention is worth a pound of cure.
Happy Computing!
In my testing, it is 10 times more important to keep your operating system, browsers, apps, and plugins up to date than it is to have the 'best' antivirus software.
How do I test for malware vulnerability? I create a dummy computer, put it on the Internet, and I visit Websites that are likely to (or are known to) infect computers with malware. Am I worried that the malware that I purposely expose my 'dummy' computer to will infect my other computers? No, because that's not how malware works anymore. Spreading to other PCs on a network is the behavior of older viruses, ones that were created more for vandalism and notoriety than to make money.
These are some of the things I learn from my malware testing:
-I find it more difficult to get my dummy computer infected than I thought it would be. The probable reason for this is that the dummy computer has not had time to collect the barnacles of spyware, adware, and browser hijacks that I end up finding on my customer's infected PCs.
-A PC with all legitimate updates applied, but no antivirus at all is much more secure than a PC with antivirus but no updates. Yes, even with top of the line antivirus, malware can get in.
The moral is: Malware defense is multi-faceted, and antivirus is typically not the most important facet. I would compare it to weight loss. Which is more important for losing weight, diet or exercise? Sadly, diet is typically more important for weight loss. In this analogy, I would compare diet to updates and exercise to antivirus.
In other words, regarding malware avoidance, an ounce of prevention is worth a pound of cure.
Happy Computing!
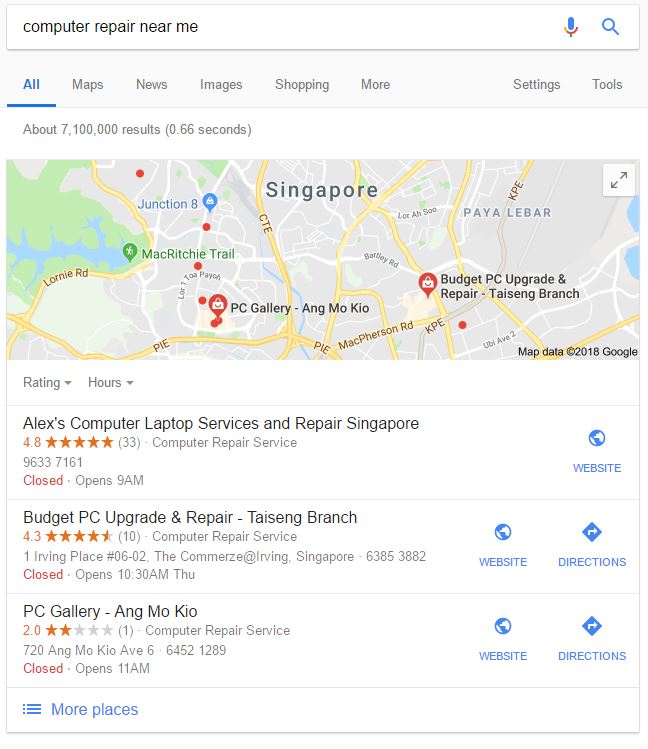
Above you see my Google Maps results when searching from my office in Minnetonka with the Epic browser. I did a local search for "computer repair near me" and the Epic browser is telling Google that I am in Singapore. If you are concerned about the ads you receive or the data that is collected about you when surfing the Web, then the Epic browser can help lessen these privacy concerns.
What Epic cannot do:
No browser alone can completely hide all of your surfing activity from (a) your ISP (e.g., Comcast, Centurylink) or (b) the government. There are cumbersome and complex ways to accomplish complete anonymity, but I'm not going to get into that here. It really is, for the most part, a situation where if you are innocent, you have nothing to fear (regarding your ISP and the government seeing your Internet use).
What Epic can do:
Using the Epic browser will make it much harder for entities like Facebook, Google, or any other advertising business that makes money from spying on your Internet use; harder to gear (possibly embarrassing) ads based on what you searched for in another browser tab, and harder to gather personal or impersonal data about you.
The main browsers (Edge, Firefox, Chrome) sell themselves as being able to offer a private browsing experience, but they typically fail to do so. Even add-ons for each of these browsers often fail to provide what the Epic browser offers as built-in features.
Some of us (myself included) have either a flippant or a 'head in the sand' attitude toward privacy concerns. But some of us are understandably a little paranoid about who is watching what we do on our computer. Using the Epic browser makes your attack surface smaller, regarding entities like Facebook or Google watching and collecting data on what we do online, and that is an important consideration with the Cambridge Analytica debacle.
Download the Epic browser here:
What Epic cannot do:
No browser alone can completely hide all of your surfing activity from (a) your ISP (e.g., Comcast, Centurylink) or (b) the government. There are cumbersome and complex ways to accomplish complete anonymity, but I'm not going to get into that here. It really is, for the most part, a situation where if you are innocent, you have nothing to fear (regarding your ISP and the government seeing your Internet use).
What Epic can do:
Using the Epic browser will make it much harder for entities like Facebook, Google, or any other advertising business that makes money from spying on your Internet use; harder to gear (possibly embarrassing) ads based on what you searched for in another browser tab, and harder to gather personal or impersonal data about you.
The main browsers (Edge, Firefox, Chrome) sell themselves as being able to offer a private browsing experience, but they typically fail to do so. Even add-ons for each of these browsers often fail to provide what the Epic browser offers as built-in features.
Some of us (myself included) have either a flippant or a 'head in the sand' attitude toward privacy concerns. But some of us are understandably a little paranoid about who is watching what we do on our computer. Using the Epic browser makes your attack surface smaller, regarding entities like Facebook or Google watching and collecting data on what we do online, and that is an important consideration with the Cambridge Analytica debacle.
Download the Epic browser here:
For most people, any one of these devices (SmartTV, Roku, or AppleTV) will be just fine. The exceptions would be:
-People who want to run a specific streaming service that is only available on certain streaming service devices, such as Amazon (until recently, when AppleTV added Amazon access) or iTunes.
-People who consume a lot of varied content, such as enjoying both YouTube and Crackle.
At this time, only the main paid channels (Netflix, Amazon, HBOGO) work reliably on all three devices. Things like YouTube, movie trailers, or viewing content on a network hard drive only work sporadically on any of these devices. For instance, the YouTube app works quite well on AppleTV, but is slow and cumbersome on a Roku. Many apps on older SmartTVs are utterly impossible to use, while newer SmartTVs do some things (YouTube and DLNA server access) better than either Roku or AppleTV.
I only mean for this to be confusing or daunting to those who (a) watch a lot of TV and (b) are picky about what they watch. Using these devices is an excellent way to increase the quantity and quality of the shows you watch, but at this time, there is no 'one size fits all' solution.
For the average person, the best choice is probably a SmartTV to start with, if for no other reason than to lessen the amount of remotes you have on the table. If a SmartTV isn't sufficient, then investigate which device will best serve your needs. This changes for the better and for the worse regularly. A current example of this is that Amazon's fire will no longer offer YouTube because of a recent battle with another tech giant, that being Google.
Feel free to ask me here or elsewhere which device is best for you.
-People who want to run a specific streaming service that is only available on certain streaming service devices, such as Amazon (until recently, when AppleTV added Amazon access) or iTunes.
-People who consume a lot of varied content, such as enjoying both YouTube and Crackle.
At this time, only the main paid channels (Netflix, Amazon, HBOGO) work reliably on all three devices. Things like YouTube, movie trailers, or viewing content on a network hard drive only work sporadically on any of these devices. For instance, the YouTube app works quite well on AppleTV, but is slow and cumbersome on a Roku. Many apps on older SmartTVs are utterly impossible to use, while newer SmartTVs do some things (YouTube and DLNA server access) better than either Roku or AppleTV.
I only mean for this to be confusing or daunting to those who (a) watch a lot of TV and (b) are picky about what they watch. Using these devices is an excellent way to increase the quantity and quality of the shows you watch, but at this time, there is no 'one size fits all' solution.
For the average person, the best choice is probably a SmartTV to start with, if for no other reason than to lessen the amount of remotes you have on the table. If a SmartTV isn't sufficient, then investigate which device will best serve your needs. This changes for the better and for the worse regularly. A current example of this is that Amazon's fire will no longer offer YouTube because of a recent battle with another tech giant, that being Google.
Feel free to ask me here or elsewhere which device is best for you.
Most inkjet printers are junk, pure and simple. The cheaper models tend to be worse, but even cost is not a reliable predictor of whether an inkjet printer will become a liability. Inkjet printer manufacturers do not put much 'love' into the design of these junkers, and most of the components are not feasible to fix if they go bad. Common problems you'll encounter with an inkjet printer are:
- Ink issues. Like having plenty of ink, but the printer says you need to go spend $40 on ink cartridges. Or, the magenta will run out and the printer won't let you print black and white (even though the black cartridge has plenty of ink left).
- Paper jams. We've been sending rockets into space for over 50 years, but printers still have trouble picking up paper and feeding it through the printer.
- Chinsey parts. Poorly planned and engineered mechanisms inside of inkjet printers are the norm. From the print head to the variously placed and configured paper trays, inkjet printers are junk.
- Larger paper tray.
- Far less risk of paper jams.
- Toner is cheaper than ink in the long run. In addition, toner requires replacement far less often and doesn't dry out when not in use.
- Laser printers tend to be more reliable in every sense.
Disclaimer: This advice is for the home user and some small business owners. If you work in a corporate environment, consult you I.T. staff regarding password management methods.
It may seem old school or not-secure, but using an alphabetized address book may be the best way to manage your passwords. Let's look at the main options for password management:
-Using one or three passwords for all the different Websites you access
-A password management program, such as LastPass
-Password encryption schemes, such as using acronyms for phrases (e.g. IALTPSAS = I'm a little teapot short and stout) and maybe adding a number to the beginning or end (e.g. 22ialtpsas).
-Keeping passwords in a Microsoft Word document on the hard drive of your computer.
Except for the first and last options in the above list, all of these are viable and relatively secure options. The problem with them is that they may not be feasible for most computer users. You probably have at least a few passwords written down, but they may be scattered about. You may have your passwords written in a book or on a sheet of paper that has lots of other information, therefore making finding your passwords more difficult.
Until other methods of authentication are available, convenient, and widely accepted, password management is here to stay. The future may bring keyboards that can sense who is using them, widely applied thumbprint scanners, facial recognition and other authentication methods that may make keeping track of passwords a smaller burden.
It may seem old school or not-secure, but using an alphabetized address book may be the best way to manage your passwords. Let's look at the main options for password management:
-Using one or three passwords for all the different Websites you access
-A password management program, such as LastPass
-Password encryption schemes, such as using acronyms for phrases (e.g. IALTPSAS = I'm a little teapot short and stout) and maybe adding a number to the beginning or end (e.g. 22ialtpsas).
-Keeping passwords in a Microsoft Word document on the hard drive of your computer.
Except for the first and last options in the above list, all of these are viable and relatively secure options. The problem with them is that they may not be feasible for most computer users. You probably have at least a few passwords written down, but they may be scattered about. You may have your passwords written in a book or on a sheet of paper that has lots of other information, therefore making finding your passwords more difficult.
Until other methods of authentication are available, convenient, and widely accepted, password management is here to stay. The future may bring keyboards that can sense who is using them, widely applied thumbprint scanners, facial recognition and other authentication methods that may make keeping track of passwords a smaller burden.
| In the meantime, for the home user and select small business person I suggest an alphabetized address book for keeping track of your passwords. Remember to leave room for new passwords when you are writing them in the book. You and only you know whether a centralized written log of passwords is a secure solution. Like with many other security risks, we often give others the keys to the castle. If you don't trust those that have access to the physical area where you keep your password book, you'll have to decide how to address that. You could hide or otherwise obfuscate the location of your password book or lock it in a safe. Whatever your method is for password management, use one that strikes a viable balance between security and convenience. Happy Computing!!! |
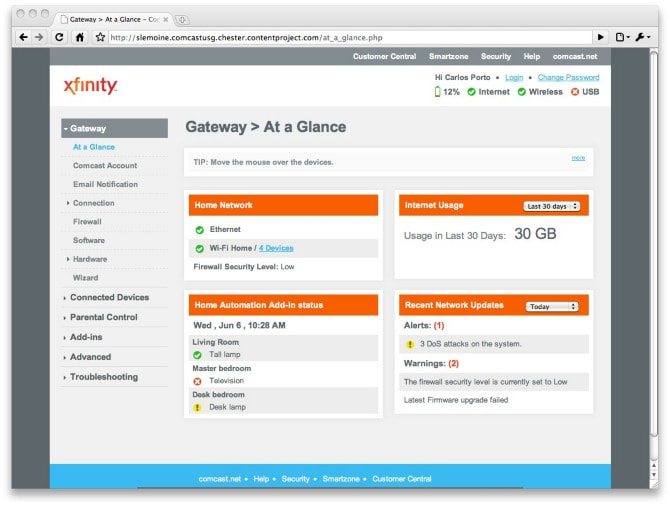
| Google WiFi is an excellent way to get great performance and features from your wireless network. I ran into a situation this week that made me feel the need to inform you of a possible problem when you install Google WiFi: you need to change or disable the WiFi sprouting from your ISP-issued gateway before setting up Google WiFi. Google's directions say to keep the same network name and password as you had before when you set up Google WiFi. This is great advice, unless your ISP-issued gateway is still sprouting it's WiFi signal. |
| For instance, if, before Google WiFi, you were using your Comcast gateway for wireless, you'll need to log into the gateway and change or turn off the wireless connection. If you don't, then both devices and humans that are connecting to your wireless network will be confused, especially if you have network printers. If you are able to locate your gateway's password and log in, you should go to Connection>>Wireless, then either disable wireless or change the name of the wireless network/s that the Comcast gateway is sprouting. |
You see, if you have shared resources (e.g., printers, network attached storage, etc...) on your network, you have to be on the same street (with different house numbers) in order to see and use network resources. If you have the same wireless network name (AKA 'SSID') and wireless password sprouting from both your gateway and Google WiFi, you probably won't have problems getting on the Internet, but you will likely have half your devices connecting to the gateway and half connecting to Google WiFi.
This is a problem because with home networking, you need to be on the same street to see each other on the network. Being on the same street on a network means that you have the same first three octets of your IP address the same. If you haven't changed or disabled the WiFi settings on your gateway before setting up Google Wifi, then half your devices may have an IP address that starts with 10 and half will have IP addresses that start with 192. If you have a wireless printer, it might end up with an IP address of 10.0.0.54 and if you're trying to print from a computer that has an IP address of 192.168.86.33, the computer will not 'see' the wireless printer, even though the wireless printer perceives itself to have a healthy connection to a network.
Possibly the most challenging part of this is locating your gateway's username and password combo. Don't forget to try the default of username: admin and password: password.
This is a problem because with home networking, you need to be on the same street to see each other on the network. Being on the same street on a network means that you have the same first three octets of your IP address the same. If you haven't changed or disabled the WiFi settings on your gateway before setting up Google Wifi, then half your devices may have an IP address that starts with 10 and half will have IP addresses that start with 192. If you have a wireless printer, it might end up with an IP address of 10.0.0.54 and if you're trying to print from a computer that has an IP address of 192.168.86.33, the computer will not 'see' the wireless printer, even though the wireless printer perceives itself to have a healthy connection to a network.
Possibly the most challenging part of this is locating your gateway's username and password combo. Don't forget to try the default of username: admin and password: password.
Brad Copeland
Gentle, no-nonsense advice and perspectives on technology.